The world is being attacked by malicious software called WannaCry ransomware. More than 104 countries have become the targets, and tens of thousands of PCs have become the victims. It is one of the largest ever cyber attacks. A latest news showed that 24 hours after the attack, it seems to be slowing, but has not stopped at all. Analysts found that the attacks may come from enterprising hackers, who want to take advantages from the weakness of PC system, particularly PCs that run on Windows operating system.
What Is WannaCry Ransomware?
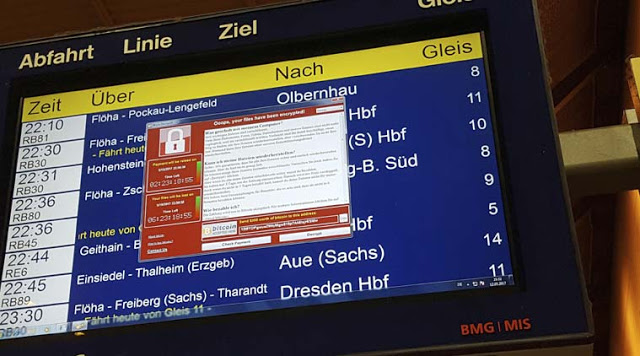
The virus attacks suddenly become phenomenal. What is WannaCry Ransomware? It is actually a virus, which attacks computers and prevents the PCs from accessing the OS. Once the computer is attacked, all of the data stored in it are encrypted. Unless the users pay certain amount of money, the data will not be opened at all. The hackers receive payment through a Bitcoin account to decrypt the files and open access to the OS.
The request is $600 in Bitcoin and the wallet is displayed on the attack messages. An interesting fact is that the initial request for the payment was only around $300 USD. Then, the group of attackers increased the ransom demands. There is still a chance that the group will keep increasing the demands. Some messages come with a threat that the users will completely lose the files in the PCs if they do not make a payment after a set timeout.
Once it attacks the computer, it cannot be killed by any anti-virus software. Using an antivirus after the attacks may even make the conditions worse. All of the files could not be opened even after the users make payments. The virus was designed to attack multiple users in multiple countries. The messages come in different languages. It means that the hackers intentionally target several countries.
The hackers also designed a way to change the users’ wallpaper with instructions on how to open the files and find the decryptor tool. However, it is almost unlikely to detect any specific culture or code page, since the hackers use universal English and Latin codepage. The user manuals come in different languages, such as Chinese, Croatian, Bulgarian, English, Filipino, Indonesia, Korean, Italian, Greek, Polish, Turkish, Swedish, Portuguese, Vietnamese, Russian, Japanese, French, German, Danish, Dutch, and many other languages.
Targets of WannaCry Ransomware Attacks
Victims of the virus attacks vary from personal computers to organizations, health facilities, and government organization. Actually, the number of victims is still controversial. As reported in Reuters, Anti-virus provider Avast estimated that the virus has attacked around 126.000 systems around the world. A team of analysts from Kaspersky Lab found that the attacks come through SMBv2 remote code execution. Most of the affected PCs run on Microsoft Windows. It predicted that the virus has attacked more than 45.000 systems in 74 countries.
Several countries have issued attack alerts to inform their citizens on the possible virus attacks. In Spain, the alert was issued along with a recommendation to install updates in Security Bulletin issued by Microsoft in March 2017. The update is one of the ways to stop the attacks. In the UK, the virus attacks 16 medical institutions. As a response, the National Health Service (NHS) also issued an alerts related to WannaCry Ransomware. Attacks were also reported in India, Russia, and Ukraine.
As reported in Kaspersky Lab website, the virus is targeting certain clusters of file formats. They include the following:
• Popular office file extensions, such as .doc, .xlsx, .ppt, .sxi
• Office formats that are nation-specific, such as .odt, .sxq, .hwp
• Archive media files, such as .rar, .mp4, .zip, .mkv, .tar, or .bz2
• Database files, such as .sql, .dbf, .odb, .myd, .accdb
• Emails, such as .eml, .pst, .edb, .msg, or .ost
• Graphic desgner files, such as .odg, .vsd, .svg, .psd
• And many more
How to Avoid WannaCry Ransomware Attacks
No single solution has been available to stop the attacks. Kaspersky offers its Kaspersky System Watcher component, which is able to rollback the changes after the attacks. However, most of the recommendations focus on the following:
• Installing the official patch from Microsoft. The patch closes vulnerability of the affected SMB server used during the attack.
• Make sure that MS17-010 security patches are properly installed and running well.
• Scanning all the systems after detecting the attacks.
• Disconnecting the infected computer from internet to prevent spreading of WannaCry Ransomware to other vulnerable computers
• Backing up all important files and data. You can use an external hard drive to backup the data. Alternatively, you can subscribe for a cloud-based backup services, such as Google Drive, Dropbox, or Apple iCloud.
• Updating the existing anti-virus regularly and periodically
• Avoiding clicking harmful links in emails
• Never visiting unsafe or unrealizable sites
• Never clicking untrusted links on social media applications
• Disabling the SMB v1
• Disabling the macros function
• Blocking 129/445 and 3389 ports
• Updating the operating system. If you still depend upon Microsoft Windows, upate to Windows 10 as soon as possible
Response to WannaCry Ransomware Attacks
Microsoft actually has acknowledged the vulnerability of file-sharing system in Windows. It issued a patch to overcome the problem in March 2017. However, most organizations have not installed the patch and kept the PCs unsupported. In addition, the old version of Windows, namely Windows XP, is not supported by the patch. The giant computer company made exceptions to address the bug.
In fact, many organizations and even government facilities still use the 16-year-old operating system. In the UK for instance, most of the attacks were found on medical facilities, where Windows XP is still the most popular OS. In response to the fact, Microsoft Corp took unusual step tp issue security updates to its system. The update aimed at addressing the problems in the older versions, including Windows XP and Windows 8. This was expected to slow the spread of the attacks.
In conclusion, the attacks are still on going. Preventing them by doing the necessary steps above is a wise option. The virus does not only target organization’s computers but also personal computers, desktops, and even smartphones that are connected to internet.